Welcome back!
This is a special edition of The Real Threat of Artificial Intelligence AI Security newsletter – dedicated entirely to the Model Context Protocol (MCP). MCP isn’t just another AI buzzword; it’s rapidly becoming the backbone of how LLMs interact with the outside world. And with that comes a flood of new attack vectors, misconfigurations, and creative exploits that most teams aren’t ready for.
| Disclaimer: I’ve started building my AI security course, where I will cover topics such as MCP security, agentic systems security, etc. If you want to sign up for the waitlist click here 🙂 |
MCP is a new (well, not so new, but still fresh) big thing in the AI/LLM world. There are thousands of MCP servers that you can connect your LLM to (refer here: https://hub.docker.com/mcp, https://mcpmarket.com/server), but have you ever wondered what security threats might arise from that solution? At the end of the day, MCP is just another layer of your software which encapsulates your APIs, etc.

But what threats exactly can occur in MCP servers?
Improper authentication
One of the main risks is exposing your MCP server publicly on the Internet – without authentication. According to this research by Knostic, hundreds of MCPs found online via Shodan are available without any type of authentication. That means attackers can use any of the tools available on the given MCP server without knowing any API keys or passwords. You can refer to this article for more information about securing access to your MCP.
New technology, old threats
Some things never change. While LLMs introduce new risks such as Prompt Injection or Excessive Agency, old vulnerabilities can still occur in LLMOps tools, MCP servers, etc. Multiple examples of RCE in MCP servers have been reported, including OS Command Injection in mcp-remote. Another example is RCE in Cursor through untrusted external data that can take control of the Cursor agent and exploit the agent’s privileges. Yet another example of RCE in MCP tooling is RCE in mcp-inspector by Anthropic.
Data exfiltration
While “traditional” apps enable developers to predict an app’s behavior in most situations, agentic systems are non-deterministic. An agent’s behavior can depend on so many factors that it’s difficult to predict all possible outcomes. Researchers from Invariant Labs have discovered that it’s possible to exfiltrate sensitive data from victims’ devices using a so-called “Tool Poisoning Attack” in which a malicious prompt is executed when calling a tool from a malicious MCP. They also found a way to access private GitHub repositories via MCP.
Tool shadowing
MCP’s flexibility, while letting agents connect to multiple tool servers, is also a hidden trap. A malicious server can shadow and hijack calls meant for legitimate tools, intercepting data or injecting responses without detection. Acuvity shows how a rogue MCP can masquerade as a trusted service, quietly turning your integration into a covert attack channel.
If you want to catch up on the MCP security, you’ll find some interesting articles, blog posts tools and research papers below:
Papers:
- From Prompt Injections to Protocol Exploits: Threats in LLM-Powered AI Agents Workflows (Ferrag, et al.)
- Model Context Protocol (MCP) at First Glance: Studying the Security and Maintainability of MCP Servers (Hasan, et al.)
- Beyond the Protocol: Unveiling Attack Vectors in the Model Context Protocol Ecosystem (Song, et al.)
- Chances and Challenges of the Model Context Protocol in Digital Forensics and Incident Response (Hilgert, et al.)
- MPMA: Preference Manipulation Attack Against Model Context Protocol
Blog posts:
- MCP Horror Stories: The Security Issues Threatening AI Infrastructure (Raina, docker.com)
- Top 10 MCP Security Risks (and How to Avoid Them) (prefactor.tech)
- ‘CurXecute’ – RCE in Cursor via MCP Auto‑Start (aim.security)
- GitHub MCP Exploited: Accessing private repositories via MCP (invariantlabs.ai)
- The Ultimate Guide to MCP Auth: Identity, Consent, and Agent Security (permit.io)
- We built the security layer MCP always needed (trailofbits.com)
- MCP Doesn’t Stand For “Many Critical Problems” … But Maybe It Should For CISOs (Forrester.com)
- MCP security vulnerabilities expose marketing technology platforms (ppc.land)
- 5 MCP security risks and mitigation strategies (techtarget.com)
- Understanding the security landscape of MCP (apideck.com)
Code & repos (be careful when running that):
- https://github.com/fkautz/safe-mcp (security framework for documenting and mitigating threats in MCP)
- https://github.com/knostic/MCP-Scanner (MCP scanner by Knostic)
- https://github.com/harishsg993010/damn-vulnerable-MCP-server/ (vulnerable MCP server)


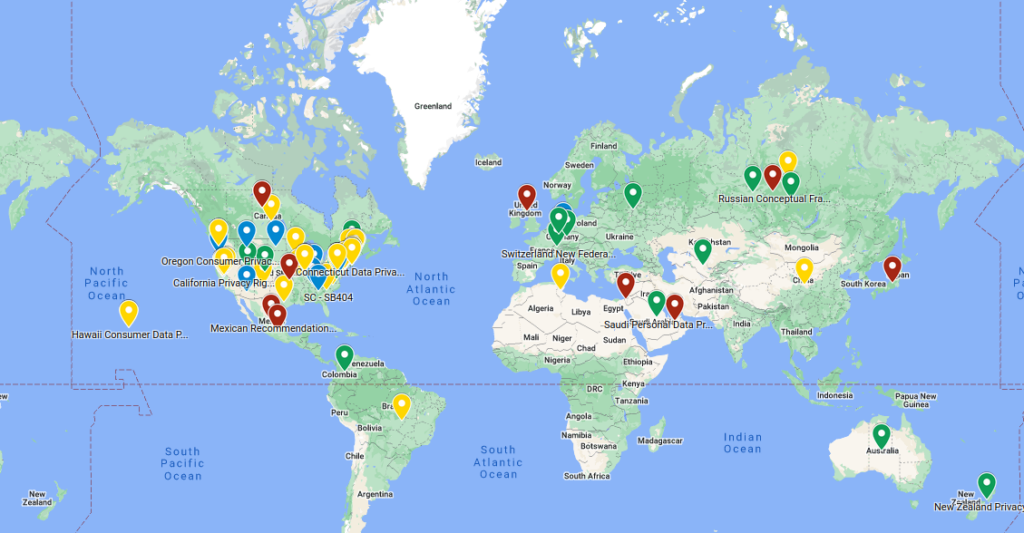
 Green: Regulation that’s passed and now active.
Green: Regulation that’s passed and now active. Blue: Passed, but not live yet.
Blue: Passed, but not live yet. Yellow: Currently proposed regulations.
Yellow: Currently proposed regulations. Red: Regions just starting to talk about it, laying down some early thoughts.
Red: Regions just starting to talk about it, laying down some early thoughts.